Introduction to End to End Secure Data Transmission

Introduction
Service providers and their technologies have been increasingly scrutinized by governments and the public due to the unfortunate consequences of their security practices—or lack thereof. One critical area to secure is commonly referred to as data-in-transit. Transmitting data over the internet, or any unsecured network, comes with inherent risks that can’t be ignored.
Unauthorized access to transmitted data is possible through an attack known as a man-in-the-middle (MITM). As the name suggests, a malicious actor intercepts communication between two parties to gain some benefit. There are many ways these attacks can occur; however, for brevity, we’ll assume unauthorized data access is both feasible and highly probable.
The solution prevents anyone intercepting the communication from understanding or manipulating the intercepted messages, regardless of the type of MITM attack. This is achieved using well-known cryptographic techniques that guarantee the authenticity, integrity, and confidentiality of the transmitted messages.
The Problem
The scenario in this discussion centers securing the communication across the internet between two participants. The issue at hand is that someone other than the intended participants could access the message and benefit from this knowledge. Below, Figure 1 illustrates a simplification of this scenario.
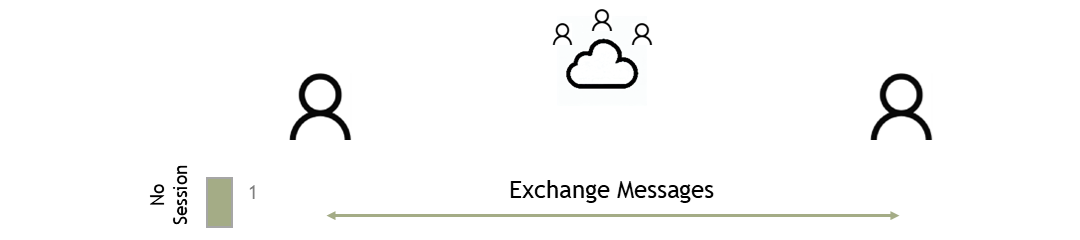
Attackers can inject themselves into three logical places: local networks and the internet. To define a sensible solution, we must assume no place is safe once the message leaves the application’s memory space. Vulnerabilities can exist in any underlying protocols and technologies used to transmit the message.
The Analysis
To solve this problem, we need a mechanism by which both ends of the communication can assert that the messages show the following properties:
- They can’t be tampered with, ensuring the original message is not read before it reaches the receiver unchanged.
- They are authentic, confirming the message was created by the sender and was intended for the receiver.
- They can’t be repudiated, meaning the participants can’t deny having sent or received them.
- They exhibit forward secrecy, ensuring the compromise of a secret does not compromise other message exchanges.
Making Progress
Let’s break down a partial solution for the first property: preventing unauthorized parties from reading or modifying
the message. Encryption can prevent unauthorized reading, while a signature or a digest can prevent tampering. However,
these primitives require a secret. Using a pre-agreed long-lived secret works, but what if it gets compromised?
Introducing ephemerality and randomness to the secret can address this concern.
Messages thus must show an additional property:
- They have perfect forward secrecy, meaning a compromised session key affects only the messages protected with that key and a compromised long-lived key doesn’t affect any previously protected messages.
Using a key exchange primitive, the Sender and Receiver can generate a common value. The output of the key exchange should not be used as the secret itself but as input to a key derivation method that uses a pseudo-random function (PRF) to generate the actual secret that becomes the session key.
To tackle tampering and forward secrecy, a key agreement procedure using key exchange and PRF primitives is needed. Figure 2 illustrates this idea.
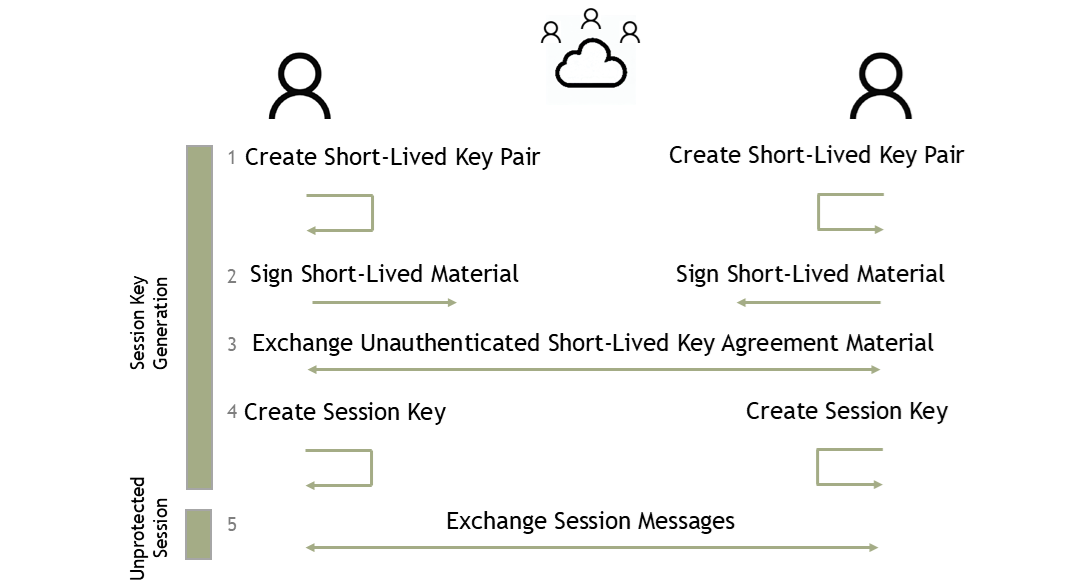
While the transmitted message is guaranteed to be protected end to end strictly speaking, the Attacker might have intercepted the previous messages carrying the key agreement material and thus enabling the manipulation of the procedure in a way that goes unnoticed by the Sender and Receiver. In this scenario, the Attacker effectively becomes the Sender, the Receiver, and/or simply an intermediary that understands the communication and thus can act on it.
This attack is attainable because neither the Sender nor Receiver are authenticated as the absence of long-lived keys would suggest. Even if they each hold their ephemeral private key, the Attacker could neglect this by generating its own ephemeral key pair impersonating the participation of the Sender or Receiver or both.
The Solution
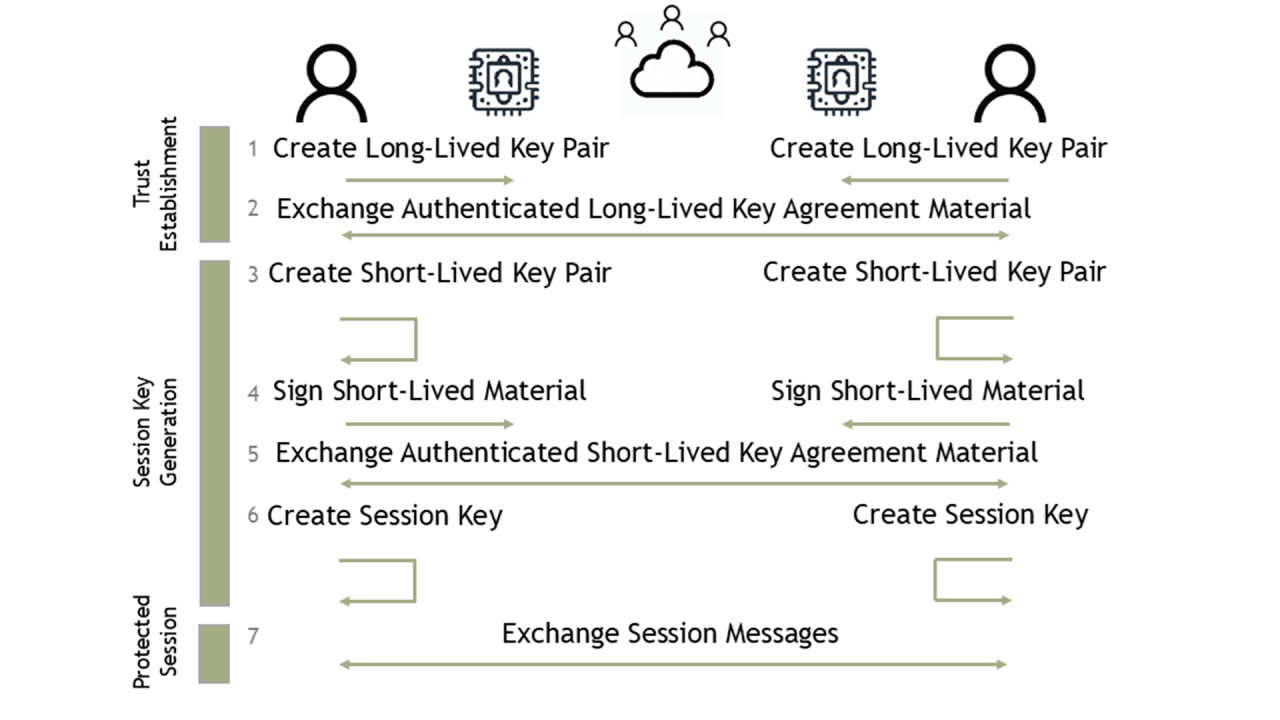
Now, let’s address the authenticity aspect. Without authentication, the Sender and Receiver don’t know who they’re communicating with. They must establish a trust mechanism where participants verify each other’s identity before any interaction. This trust establishment involves exchanging:
- A public key.
- Proof of possession of the associated private key.
- Key agreement procedure parameters.
Trust can be established directly (e.g., face-to-face interactions) or indirectly (e.g., through a trusted Certificate Authority). Figure 3 describes this solution.
The use of authenticity unveils a fourth desired property to messages flowing between the participants:
- Once done, a participant cannot deny their participation in the message exchange.
This is accomplished by participants demonstrating possession of a private key.
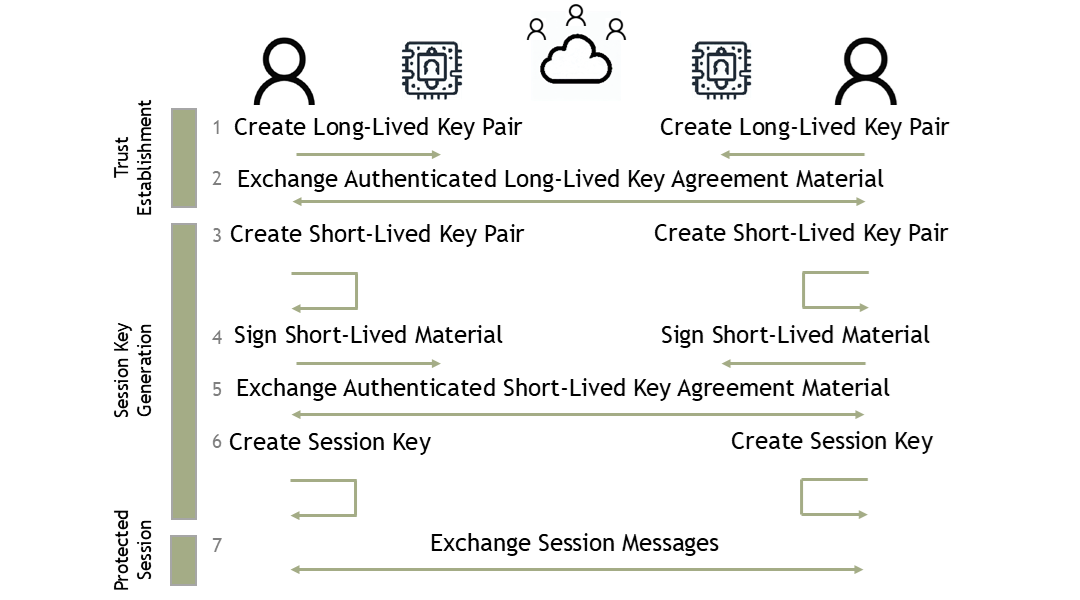
Participants must set up long-lived secrets in secure places like Trusted Platform Modules (TPMs) or Hardware Security Modules (HSMs). This ensures only the intended application accesses the secret. In some contexts, it might be acceptable for only one participant to be authenticated.
Conclusion
Given the evolving nature of cyberattacks and increasing data privacy regulations, addressing end-to-end traffic protection is crucial for any digital service relying on data transmission. This article presented proven industry practices, concepts, and considerations for solving this common problem.
The key security properties that data in transit must have:
- Authenticity.
- Tamper Proof (Integrity and Confidentiality).
- Non-Repudiation.
- Perfect Forward Secrecy.
These security properties can be achieved by:
- Establishing a Trust Relationship.
- Defining and Executing a Key Agreement Procedure.
References
- Elaine Barker (NIST), Lily Chen (NIST), Allen Roginsky (NIST), Apostol Vassilev (NIST), Richard Davis (NSA). NIST, “Recommendation for Pair-Wise Key-Establishment Schemes Using Discrete Logarithm Cryptography”, Revision 3, April 2018, csrc.nist.gov/pubs/sp/800/56/a/r3/final
- Elaine Barker (NIST), Lily Chen (NIST), Richard Davis (NSA). NIST, “Recommendation for Key-Derivation Methods in Key-Establishment Schemes”, Revision 2, August 2020, csrc.nist.gov/pubs/sp/800/56/c/r2/final
- Lily Chen (NIST). NIST, “Recommendation for Key Derivation Using Pseudorandom Functions”, Revision 1 Update 1, August 2022, csrc.nist.gov/pubs/sp/800/108/r1/upd1/final
- H. Krawczyk (IBM Research), P. Eronen (Nokia). IETF, “HMAC-based Extract-and-Expand Key Derivation Function (HKDF)”, May 2010, datatracker.ietf.org/doc/html/rfc5869
Disclaimer
All content provided in this article is exclusively for informational purposes only. The source for the making of this content is information of public domain as detailed in the references.
The owner of this article makes no representations as to the accuracy or completeness of any information presented. The owner will not be liable for any errors or omissions in this information nor for its availability, as well as not liable for any losses or damages resulting from the use of this information.