Overview — Web of Trust



Problem Statement
Contextual data to deliver personalized experiences constitutes an essential need of modern digital ecosystems that increasingly rely on autonomous software entities—including AI agents, applications, and services. This data is often sensitive and owned by individuals or organizations. However, enabling these autonomous entities to access such data dynamically at scale, in a secure manner, and while preserving privacy and transparency across multi-entity operations, presents fundamental challenges that existing industry standards fail to adequately address.
Three fundamental challenges prevent autonomous entities from operating securely at scale:

-
Scalable Dynamic Data-Access: Agents dynamically encounter new data sources during operation based on evolving processing needs, making pre-established relationships increasingly impractical to scale when serving millions of users across potentially hundreds or thousands of data providers
-
On-the-Fly Trust Verification: Without pre-established trust credentials, each data provider must independently verify an autonomous entity’s legitimacy and trustworthiness on-the-fly prior to authorizing data access, but traditional manual verification processes cannot scale to real-time requirements, creating redundant overhead and operational bottlenecks across data providers
-
Multi-Entity Data-Processing Transparency: Autonomous operations typically involve multiple entities working together—agents coordinating with third-party services, LLMs, and data processors—yet users lack visibility into this processing chain, cannot grant granular permissions to each participant, or maintain accountability for operations across the ecosystem
AI Agent View Autonomous entities face a critical operational constraint: they must access sensitive data from numerous providers to function effectively, yet each provider requires confidence in the entity’s trustworthiness. Traditional approaches require manual registration with each data provider—establishing credentials, undergoing verification, and negotiating access terms. This model fails at scale: an agent serving millions of users cannot feasibly pre-register with every potential data source, especially when processing requirements emerge dynamically during operation.
User View Users face dual challenges when engaging autonomous entities. First, before granting data access, they must evaluate an unknown agent’s legitimacy, organizational backing, and security practices—yet lack mechanisms to verify these claims. Second, users remain unaware of the complete processing chain, exposing their data to unknown third-party services, LLMs, and processors without explicit consent. This opacity prevents assessing privacy risks or establishing accountability, leaving users unable to protect their privacy or exercise meaningful control.
Data Provider View Data providers face a real-time verification challenge: they must dynamically evaluate an entity’s trustworthiness at the moment of first data access request, often without prior relationship or interaction history. Current approaches lack common industry-adopted, programmatic mechanisms to verify an unknown entity’s legitimacy, organizational backing, and user authorization in real-time. This forces data providers to choose between denying access (blocking legitimate use cases) or implementing manual registration processes that cannot scale for autonomous operations.
Solving these three interconnected challenges—scalable dynamic data access, on-the-fly trust verification, and multi-entity transparency—requires a comprehensive framework that enables dynamic trust establishment, real-time verification, and transparent multi-entity coordination while maintaining user control and cryptographic accountability throughout the data lifecycle.
System Overview
The Web of Trust (WoT) system addresses the challenges outlined in the problem statement by creating a comprehensive framework for managing trust, relationships, consent, and data access across organizations, users, autonomous entities, traditional applications, and services.
WoT operates as a trusted intermediary that integrates existing trust establishment mechanisms (e.g., X.509 Certificate Chains, OpenID Federation) with OAuth2/OIDC protocols while extending them to support dynamic autonomous entity operations, explicit multi-party relationships, granular consent management, and cryptographically accountable data access throughout the entire lifecycle.
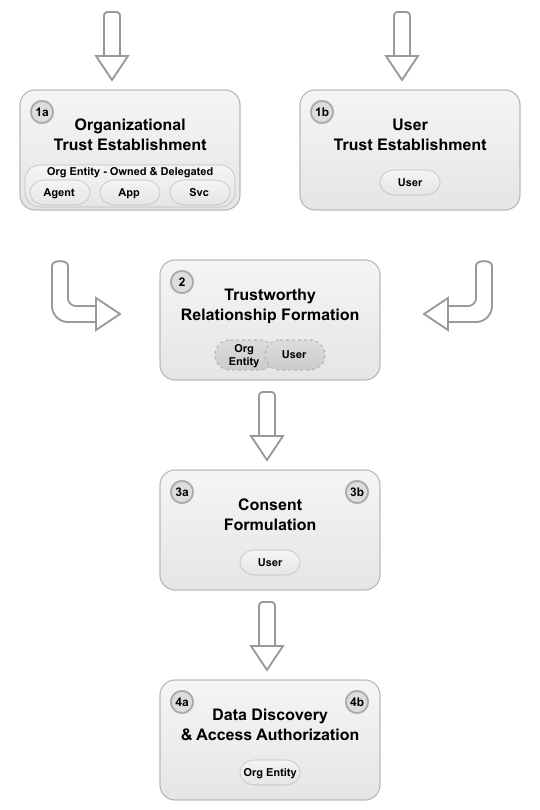
Details
The diagram illustrates WoT’s end-to-end operation through four interconnected phases:
1.a. Organizational Trust Establishment: Organizations undergo identity verification through external trust anchors (X.509, OpenID Federation) or WoT-orchestrated processes, resulting in verified WoT registration with cryptographic credentials. Once registered, organizations can create delegated entities (agents, applications, services) that inherit trust from the parent organization while maintaining their own authentication credentials and operational independence. Each organizational entity generates cryptographic key pairs and registers their public keys with WoT, with a strong recommendation for their private keys to be managed through secure crypto modules (e.g., HSM, TPM, Keychain) for subsequent authentication.
1.b. User Trust Establishment: Users establish their identity through FIDO2/WebAuthn authentication, with optional identity verification for enhanced trust relationships. Users can register with or without verified identity, though verification enables access to more trust-sensitive interactions. Even without formal identity verification, the FIDO2 authenticator provides cryptographic proof that the current user is the same person who registered the account and possesses the registered device, establishing the foundation for subsequent consent and authorization decisions.
2. Trustworthy Relationship Formation: Organizations and users, having already established their trust credentials independently, can now form explicit relationships within WoT. Prior to approving any relationship, WoT verifies the requested relationship parameters against the parties’ pre-existing trust establishment proofs and credentials. WoT registers approved relationships with defined scopes, constraints, and cryptographic accountability, enabling subsequent mediation of consent and data access requests based on these pre-established trust relationships.
3a. WoT Consent Formulation: When an organizational entity requests access to user data, WoT implements a two-layer consent architecture. In the WoT layer, WoT presents a granular consent request providing detailed information about which specific organizational entities (not just the parent organization) will access data, what specific data types each entity requires, conditions and constraints on data usage, evidence of why these entities are trustworthy based on their verified credentials and relationship parameters, and the purpose and duration of data access. Users can grant, deny, or conditionally approve consent with fine-grained control over data sharing across multiple entities.
3b. IdP Consent Formulation: In the IdP layer, users interact with the Identity Provider’s standard OAuth2 consent interface, which serves as the actual authorization mechanism for data access. WoT’s consent layer acts as an enhancement wrapper around this traditional OAuth2 consent, providing multi-entity visibility and trustworthiness assessment.
4a. Data Discovery (Optional): After consent is obtained, organizational entities may query WoT to discover what data types are available for specific users within their established relationship. WoT returns available data types based on the user’s connected data providers and the granted consent permissions, allowing entities to proactively determine data availability before requesting access. Entities that already know the specific data types they need may skip discovery and proceed directly to data access, though they will only learn of data unavailability when the access request returns an unavailable response.
4b. Data Access Authorization: With consent in place, WoT authorizes organizational entities to access the specified user data. WoT retrieves data from user-authorized sources, validates that the requesting entity’s credentials and session are current and valid, verifies the access complies with consent parameters and relationship constraints, and securely delivers the data through end-to-end encrypted channels. Metadata of every data access operation is cryptographically logged for auditability, enabling users to review which entities accessed what data types and when, with the ability to revoke access or modify consent at any time.
This integrated approach ensures that trust flows seamlessly from external verification through relationship formation, consent management, and data access, enabling secure autonomous operations while maintaining cryptographic accountability and user sovereignty over their data and digital relationships.
Participating Entities
The Web of Trust ecosystem comprises multiple entity types organized in three concentric layers: External (where third-party entities provide trust services), Identity & Relationships (where organizations and users establish verified identities and relationships), and Web of Trust (where WoT mediates relationships, consent, and data access).
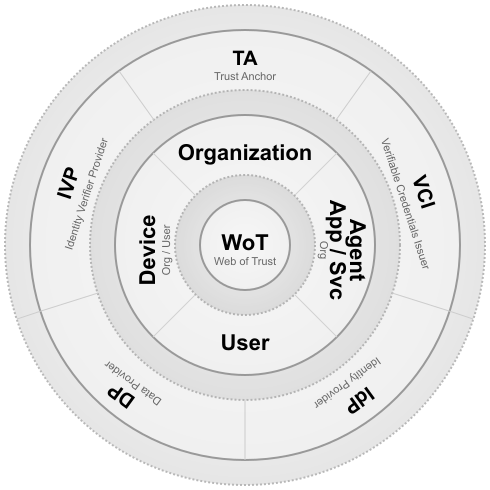
Entity Categories
The participating entities are organized into two primary categories:
Registered Entities: Digital identities established and managed by WoT, including organizations, users, and their delegated entities (agents, applications, services, devices). These entities can form relationships, grant consent, and access or provide data within the trusted ecosystem.
Supporting Entities: External entities that provide trust establishment, consent management, and data access services. These entities operate independently of WoT but integrate with the system to enable its comprehensive trust framework.
Registered Entities
User Entities
User: Individual entity that owns personal data and establishes relationships with organizational entities requiring data access. Users have:
- Relationships with different organizations and their entities
- Authentication capabilities through FIDO2/WebAuthn credentials
- Regulatory privacy rights (GDPR, CCPA, HIPAA) that shape consent and data handling
When granting data access consent, users authenticate using FIDO2 to create a cryptographic binding between their verified identity and consent acceptance
User Device: Physical or virtual device owned by an individual (smartphone, tablet, laptop) that, when registered with WoT, strengthens security posture through cryptographic device authentication.
Organization Entities
Organization: Business entity that owns entities (agents, applications, services) that perform tasks for users. Organizations have:
- Verified identity through external trust anchors to establish WoT registration
- Authentication capabilities through cryptographic credentials linked to trust anchors
- Ownership of delegated entities that inherit organizational trust and that act on its behalf
- Liability for actions of their delegated entities through cryptographic attestation of ownership
Agent: Entity with varying degrees of independence that makes context-driven decisions and takes actions within well-defined parameters. Agents have:
- Relationships with users to offer AI-powered service
- Interactions across multiple platforms with other agents, applications, or services of the owning organization or of a third party
- Responsibilities that may require dynamic access to contextual data from multiple sources
Agents represent the primary use case driving WoT’s design, as AI agents particularly benefit from dynamic data access capabilities, cross-organizational operation support, and verifiable accountability mechanisms that enable independent operation while maintaining user control.
Application (App): Entity with specific functionality that operates on behalf of an organization to provide services to users. Applications have:
- Relationships with users to deliver application functionality
- User interfaces that operate within single platforms or environments
- Predetermined functions with well-defined behavior patterns
Service (Svc): Backend software entity that provides specific functionality without direct user interaction. Services have:
- Relationships with users to offer backend processing
- Continuous or on-demand operations to process data, perform computations, or integrate systems
Organization Device: Physical or virtual device entity representing server infrastructure or enterprise hardware owned by an organization that, when registered with WoT, strengthens security posture through cryptographic device authentication.
Supporting Entities
Supporting entities operate in external layers and provide essential services that WoT integrates into its trust framework. These entities are grouped by the lifecycle phases where they participate.
Trust Establishment Phase
Trust Anchor (TA): Root authority in a trust hierarchy that establishes foundational trust. Trust Anchors may include:
- Certificate Authorities (CA) in X.509 PKI ecosystems
- Trust anchors in OpenID Federation hierarchies
- Other recognized sources of cryptographic identity verification
Identity Verification Provider (IVP): External service that verifies the legal or real-world identity of users or organizations. IVPs may include:
- Know Your Customer (KYC) providers for individual identity verification
- Know Your Business (KYB) providers for organizational identity verification
- Document authentication services for credential verification
- Biometric verification services for liveness detection
Verifiable Credential Issuer (VCI): Entity that issues cryptographically signed credentials attesting to specific claims. VCIs may include:
- Financial institutions issuing creditworthiness credentials
- Government agencies issuing identity credentials
- Academic institutions issuing educational credentials
- Professional licensing bodies issuing certifications
Consent Formulation Phase
Identity Provider (IdP): External service that manages user authentication and authorization for data access. IdPs may include:
- Enterprise identity services (e.g., Microsoft Entra ID, Okta)
- Consumer identity platforms (e.g., Google Identity Services, Apple Sign-In)
- Federated identity systems supporting SAML/OIDC protocols
- Social identity providers for authentication delegation (e.g., Facebook Login, LinkedIn Sign-In)
Identity Providers have a trust relationship with WoT rather than establishing direct trust relationships with every potential agent.
Data Access Authorization Phase
Data Provider (DP): External entity that hosts or controls user data that organizational entities wish to access. Data Providers may include:
- Financial institutions providing account and transaction data
- Healthcare systems providing medical records and health data
- Fitness platforms providing wellness and activity data
- Cloud storage services providing user-managed files
Data Providers trust IdP-issued tokens rather than establishing direct trust relationships with every potential agent.
Entity Relationships
These entities interact across the three trust layers:
-
External Trusted Root, Consent & Data Access: Trust Anchors, Identity Verification Providers, and Verifiable Credential Issuers establish foundational trust for initial registration. Identity Providers manage OAuth2 authorization, while Data Providers host user data and enforce access control.
-
Trusted Identity & Relationship: Organizations and Users register with WoT using credentials verified by the External Trusted Root, then form explicit relationships defining scopes, constraints, and permissions for data access.
-
Trusted Web: This layer brings everything together—Organizations’ delegated entities (Agents, Applications, Services, Devices) use established relationships to request data access, navigate WoT’s consent framework, obtain IdP authorization, and retrieve data from Data Providers, all mediated by WoT’s orchestration.
WoT orchestrates interactions between these entities, ensuring that trust established in external systems flows through relationship formation and granular consent to secure data access decisions within the trusted web.